An interesting TCP handshake
The TCP three-way handshake
The three-way TCP handshake is a very interesting artifact for analyzing any TCP connection. Besides the initial window size announced by the client and server, the TCP options are always worth a look to understand how the client and server TCP/IP stacks (or any kind of layer 4 devices that interfere with the packets during transmission) behave. A couple of options are usually found in the initial SYNs. Most importantly are the TCP maximum segment size, the support of selective acknowledgements (SACKs), the window scale factor and TCP timestamps.
Piggybacked SYN
Normally during the handshake, no data is yet transferred. In one recent trace, I captured on a mac OS system I found an interesting use of the three-way handshake, basically piggybacking data in the initial client SYN packet. This is still quite rare so let's examine the trace in detail.
The concerned TCP connection was initiated by Apple Spotlight which connects to Apple servers to retrieve online results for the current search query in Spotlight.
In the first packet of the TCP, connection Spotlight sends a TCP SYN packet with a piggybacked TLS Client Hello. This allows Spotlight to save at least one round trip time (potentially retransmissions) between server and client thus making the connection initiation quicker as a normal TLS connection set up.
Usually, the TCP/IP stack would first complete the three-way handshake and then send a TLS client hello. The sent data would then be acknowledged by the server before sending a Server Hello TLS packet.
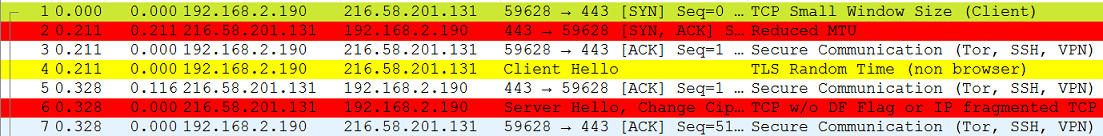
This corresponds to the following schema:
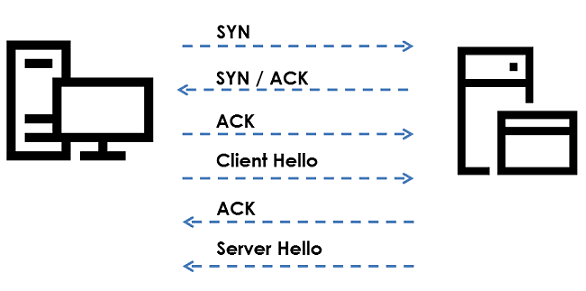
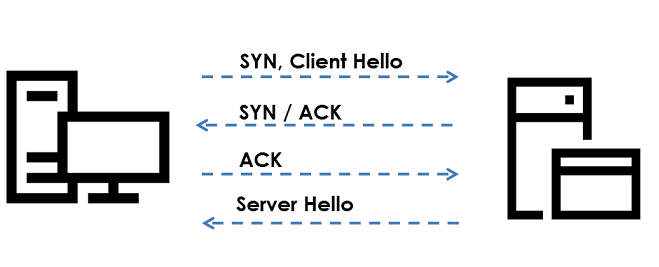
The connection at hand avoids the additional TLS Client Hello and server acknowledgement.
This corresponds to the following schema:
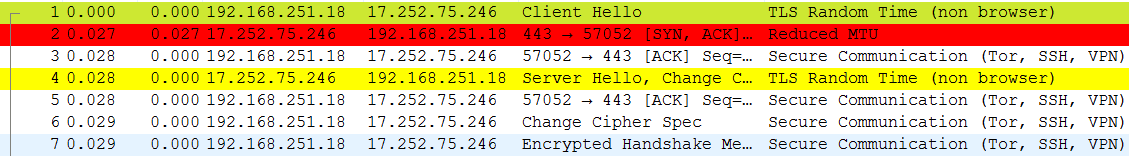
Looking at the SYN packet details, it is more visible that TLS is transmitted in the SYN.
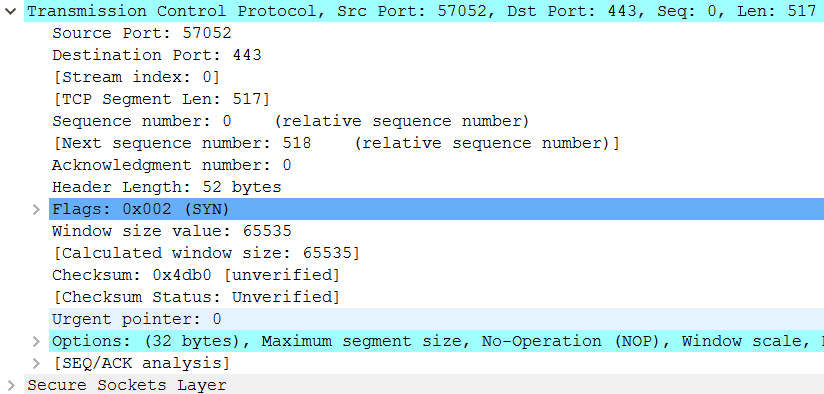
Fast open cookie
A hint on what is happening here is the option "Fast Open Cookie" present in the TCP options. Which allows the client to authenticate itself to the webserver in the initial SYN packet. The specification of the TCP fast Open also allows exactly what is visible in the trace - to sent data already in the initial SYN packet. TCP fast open was only quite recently specified in the RFC7413
Trace files
Here is the piggy backed trace file fast-open.pcapng and here a normal connection startup normal.pcapng for comparison.
Learn more
To learn more about analyzing packets to solve network problems and prove with network analysis that performance issues are not the fault of the network go ahead and book a network analysis training.
You also might be interested in learning about network security and protecting your network where it matters by booking the brand new CYSEC+ course.


