Packet List
Packet Safari allows exploring a list of packets and filtering it
Filtering packets
One of the most useful features of PacketSafari is the ability to filter packets. Filtering packets allows you to focus on specific packets and quickly analyze them. In this article, we will discuss the 10 most commonly used use cases for filtering packets.
Protocol-based filtering
One of the most basic uses of filtering packets is to filter based on a specific protocol. Protocol-based filtering is useful when you want to focus on a specific type of traffic.
Example filter: http
This filter will display only HTTP traffic in the capture.
IP-based filtering
Another common use case for filtering packets is IP-based filtering. You can filter packets based on their source or destination IP address. This type of filtering is useful when you want to focus on traffic to or from a specific IP address.
Example filter: ip.addr == 192.168.0.1
This filter will display only packets that have a source or destination IP address of 192.168.0.1.
Port-based filtering
Port-based filtering is another useful way to filter packets. You can filter packets based on their source or destination port number. This type of filtering is useful when you want to focus on traffic to or from a specific port.
Example filter: tcp.port == 80
If both source and destination port should be 123, you can use tcp.port === 123 (three equals)
This filter will display only packets that have a source or destination port of 80, which is the default port for HTTP traffic.
Protocol and port-based filtering
Protocol and port-based filtering can be used to filter packets based on both the protocol and port number. This type of filtering is useful when you want to focus on a specific type of traffic on a specific port.
Example filter: tcp.port == 80 && http
This filter will display only packets that have a source or destination port of 80 and that are HTTP traffic.
Time-based filtering
Time-based filtering allows you to filter packets based on the time they were captured. This type of filtering is useful when you want to focus on a specific time period.
Example filter: frame.time >= "Mar 21, 2023 10:00:00" && frame.time <= "Mar 21, 2023 11:00:00"
This filter will display only packets that were captured between 10:00 and 11:00 on March 21, 2023.
Filter by length
Filtering packets by length allows you to focus on packets of a specific length. This type of filtering is useful when you want to focus on packets that are either too large or too small.
Example filter: frame.len > 1000
This filter will display only packets that have a length greater than 1000 bytes.
Filtering by source MAC address
MAC-based filtering allows you to filter packets based on their source MAC address. This type of filtering is useful when you want to focus on traffic from a specific device.
Example filter: eth.src == 00:11:22:33:44:55
This filter will display only packets that have a source MAC address of 00:11:22:33:44:55.
Filtering by destination MAC address
Destination MAC-based filtering allows you to filter packets based on their destination MAC address. This type of filtering is useful when you want to focus on traffic going to a specific device.
Example filter: eth.dst == 00:11:22:33:44:55
This filter will display only packets that have a destination MAC address of 00:11:22:33:44:55.
Filtering by VLAN tag
VLAN-based filtering allows you to filter packets based on their VLAN tag. This type of filtering is useful when you want to focus on traffic in a specific VLAN.
Example filter: vlan.id == 100
This filter will display only packets that belong to VLAN ID 100.
Filtering by custom expressions
Custom expressions allow you to create filters based on any combination of protocol fields. This type of filtering is useful when you need to create a custom filter that is not covered by the pre-defined filters.
Example filter: tcp.flags.syn == 1 && tcp.flags.ack == 0
This filter will display only packets that have the SYN flag set and the ACK flag not set, which indicates a SYN-only packet.
Filtering by packet direction
You can filter packets based on their direction, whether they are incoming or outgoing. This type of filtering is useful when you want to focus on packets flowing in a specific direction.
Example filter: ip.src == 192.168.0.1 && ip.dst == 192.168.0.2
This filter will display only packets that have a source IP address of 192.168.0.1 and a destination IP address of 192.168.0.2, regardless of their direction.
Filtering by HTTP status code
You can filter HTTP packets based on their status code, whether it is a 200 OK or a 404 Not Found. This type of filtering is useful when you want to focus on HTTP responses with a specific status code.
Example filter: http.response.status_code == 404
This filter will display only HTTP responses with a status code of 404.
Filtering by SSL version
You can filter SSL packets based on their version, whether it is TlS1.2 or TLS1.3. This type of filtering is useful when you want to focus on SSL traffic with a specific version.
- TLS1.2:
tls.handshake.version == 0x0303 and !tls.handshake.extensions.supported_version == 0x0304 - TLS1.3:
tls.handshake.version == 0x0304
This filter will display only SSL packets with a version of TLSv1.2.
Filtering by HTTP method
You can filter HTTP packets based on their method, whether it is a GET or a POST request. This type of filtering is useful when you want to focus on HTTP requests with a specific method.
Example filter: http.request.method == POST
This filter will display only HTTP requests with a method of POST.
Filtering by IP protocol
You can filter packets based on their IP protocol, whether it is TCP, UDP, ICMP, or any other protocol. This type of filtering is useful when you want to focus on packets of a specific IP protocol.
Example filter: ip.proto == 1 (icmp)
This filter will display only ICMP packets in the capture.
Filtering by DNS query or response
You can filter DNS packets based on whether they are queries or responses. This type of filtering is useful when you want to focus on DNS queries or responses.
Example filter: dns.flags.response == 1
This filter will display only DNS responses in the capture.
Filtering by packet payload
You can filter packets based on their payload, whether it contains a specific string or pattern. This type of filtering is useful when you want to focus on packets that contain specific data.
Example filter: http contains "password" or frame contains "password"
Be careful, nowadays many payloads are encrypted. If you decrypted the tracefile, you can then search in the decrypted payload, but you have to make sure to search in the correct layer (the reassembled one). Usually searching in the higher layers (not frame, ip, or tcp) will result in the best result.
This filter will display only HTTP packets that contain the string password in the payload.
Filtering by packet fragmentation
You can filter packets based on whether they are fragmented or not. This type of filtering is useful when you want to focus on fragmented or unfragmented packets.
Example filter: ip.flags.mf == 1
This filter will display only IP packets that are fragmented.
Filtering for a subnet
You can use the === operator to compare values of a particular field in the packets. To filter for a range of IP addresses in a subnet, you can use the CIDR notation with the ip.addr field. ip.addr is actually a shorthand for ip.src == x or ip.dst == x
For example, to filter for all packets within a subnet with a CIDR notation of 192.168.1.0/24, you can use the filter ip.addr === 192.168.1.0/24. This will display all packets that have a source and destination IP address in the range of 192.168.1.0 to 192.168.1.255.
This filter can be useful for troubleshooting network issues in a specific subnet, such as identifying sources of high network traffic or identifying devices with abnormal network behavior. By filtering for packets within a specific subnet, you can narrow down the scope of your analysis and focus on the packets that are most relevant to your investigation.
Intelligent filter completion
Deep link to filtered packets
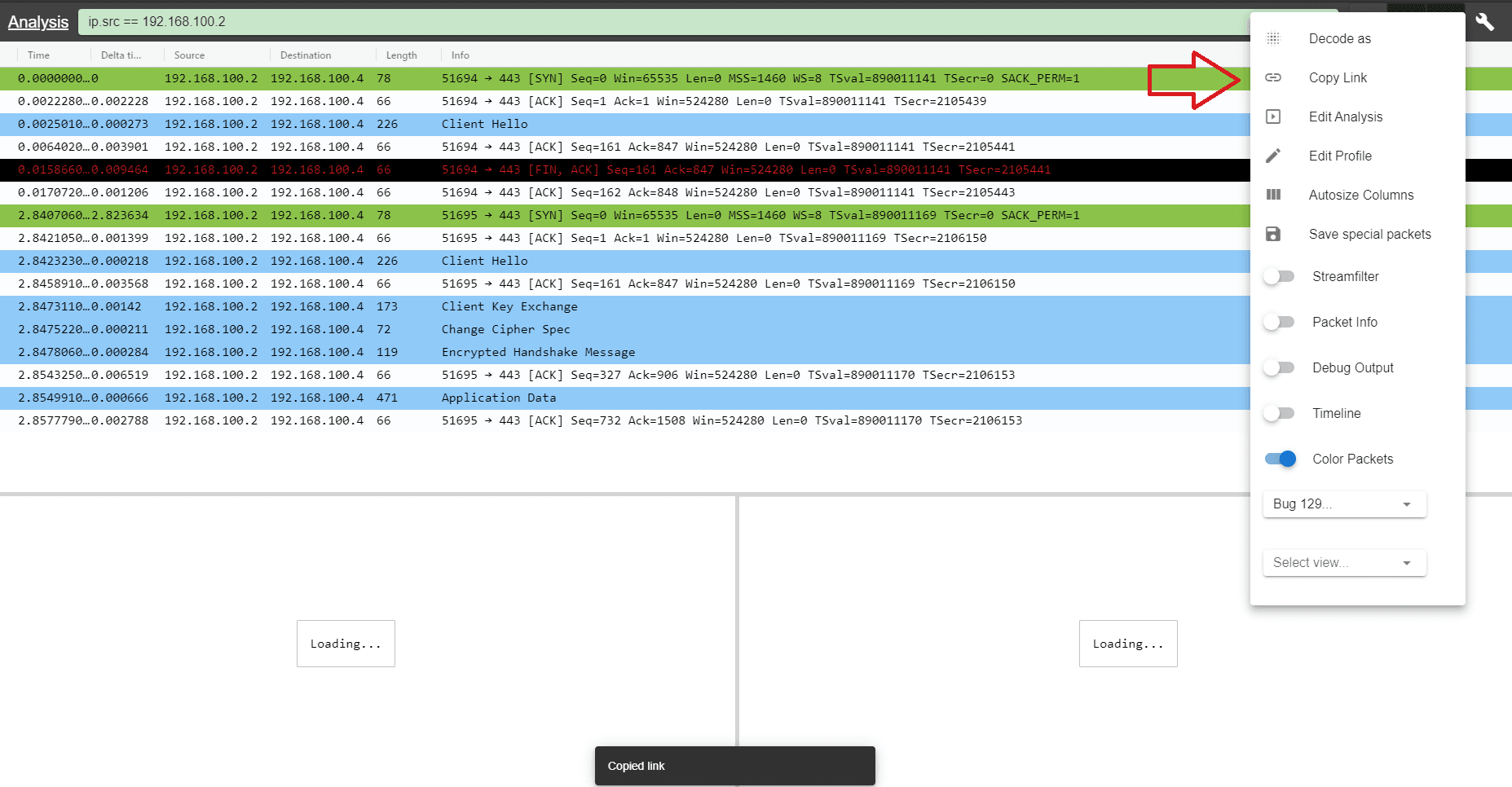
Right Click Actions
There are several actions possible right clicking on a specific packet (row) or even column within a packet
- toggle time reference
- explain packet
- follow
- prepare filter
- apply filter
- conversation filter
- mark packet (e.g. for export)
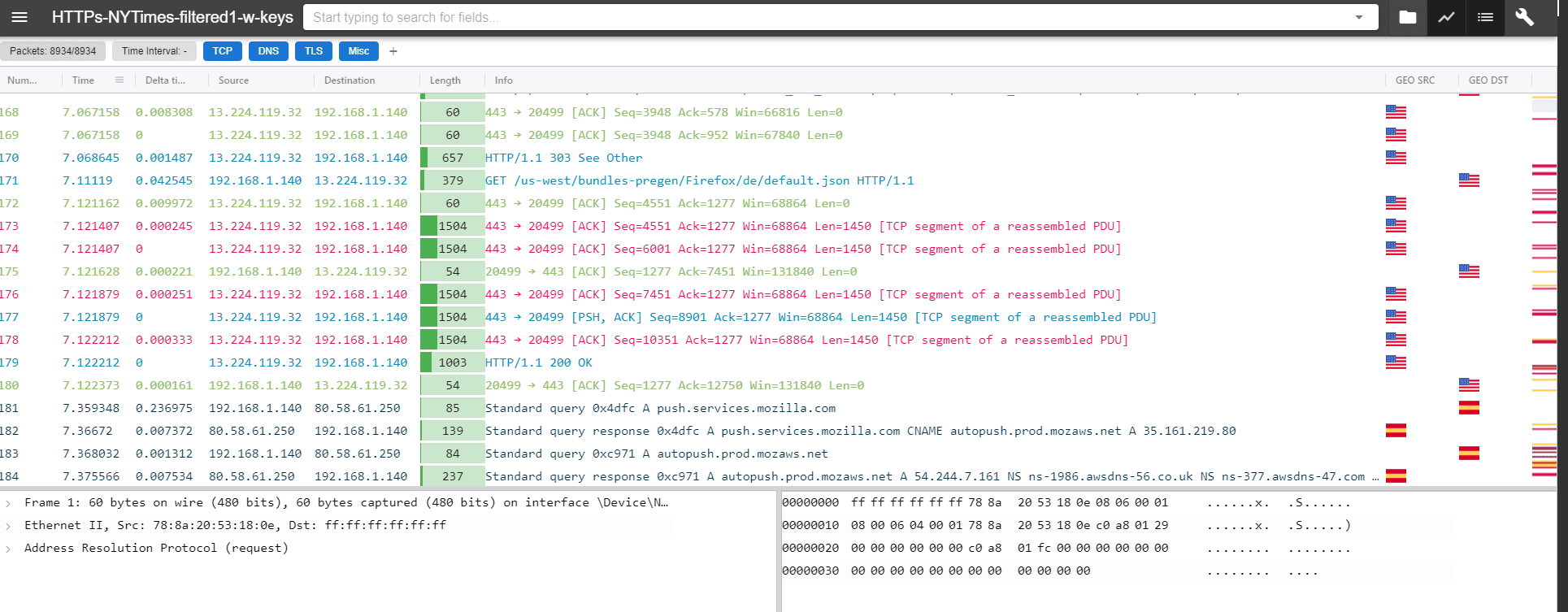
Advanced rendering
Advanced rendering allows you to change the rendering of the columns in the packet list. In this example country names are shown as flags and the ethernet length column is displayed using colors and an indicator shows the longest packet in the trace.
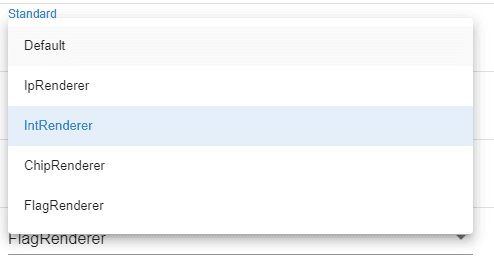
To use advanced rendering you need to enable it for the profile
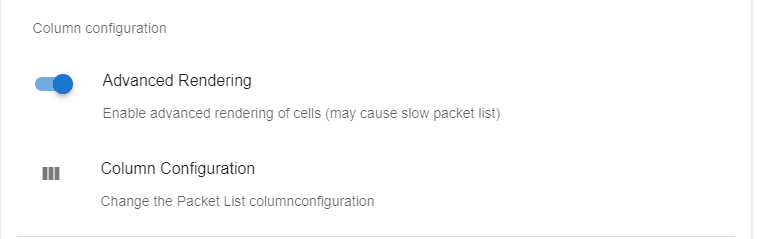
Then you need to specify which columns should be rendered differently in the column configuration
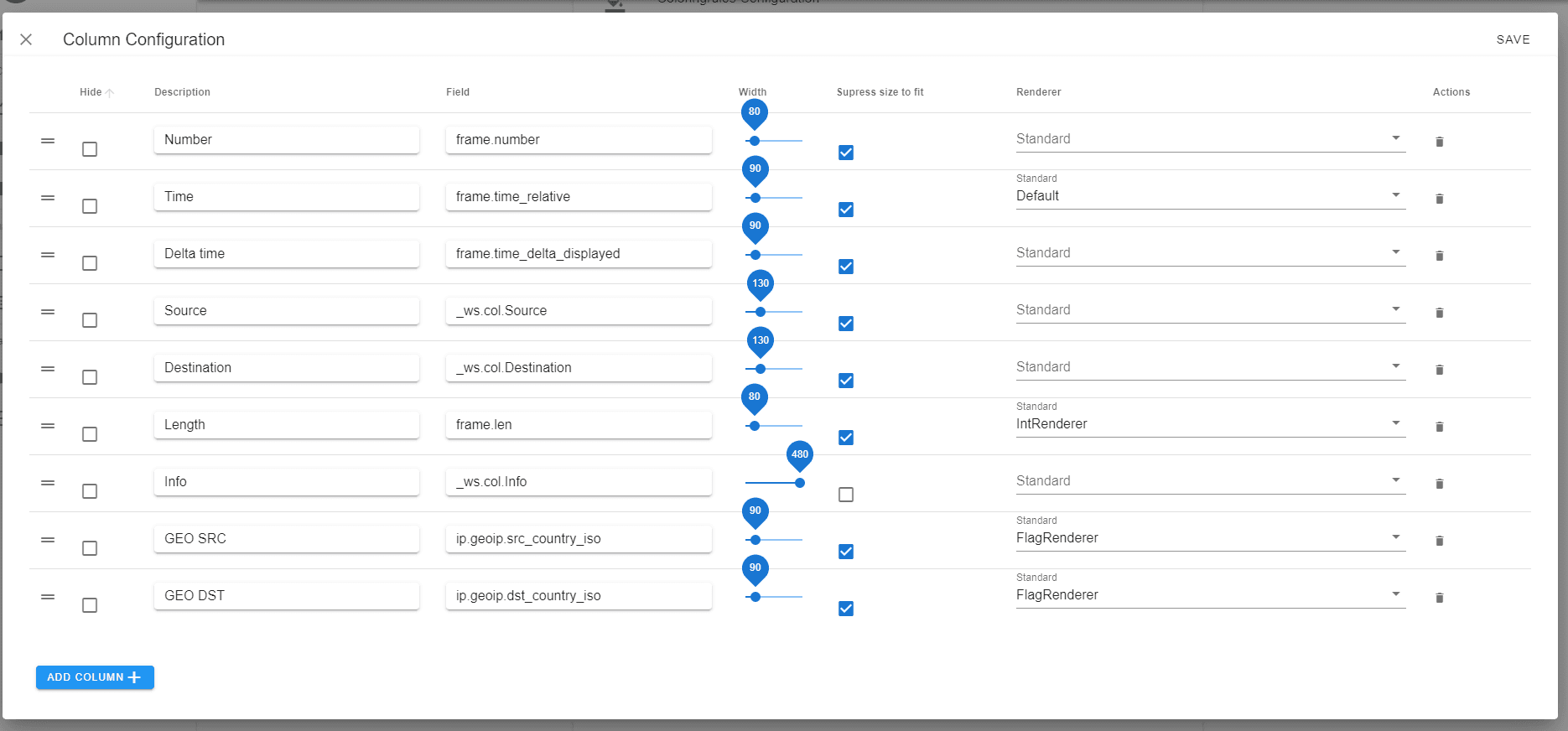
Currently the following renderers are available. Some renderers may only work with certain fields or only with indexed fields (e.g. the IntRenderer)