PCAP Search
From the PCAP list you search through all your files, public files, and files that you have read access to
ID Search
You can search by PCAP ID. The PCAP ID uniquely identifies your PCAP in the system.
_id:ZmFzdC1vcGVuLnBjYXBu
Owner search
By using the username field you can search for PCAPs uploaded by a certain user.
username: john
Metadata search
You can search files via their metadata. For example, meta information extracted from the PCAP. Metadata search allows you to use Elastic Search query strings to search through your PCAPs.
You can search for exact matches strings or date fields for ranges.
- Original PCAP file name:
origname:"fast-open.pcapng" - SHA1:
sha1:"34e9e6c2839ff461b70f815515cb6c3cd1551fb3" - Data bit rate range:
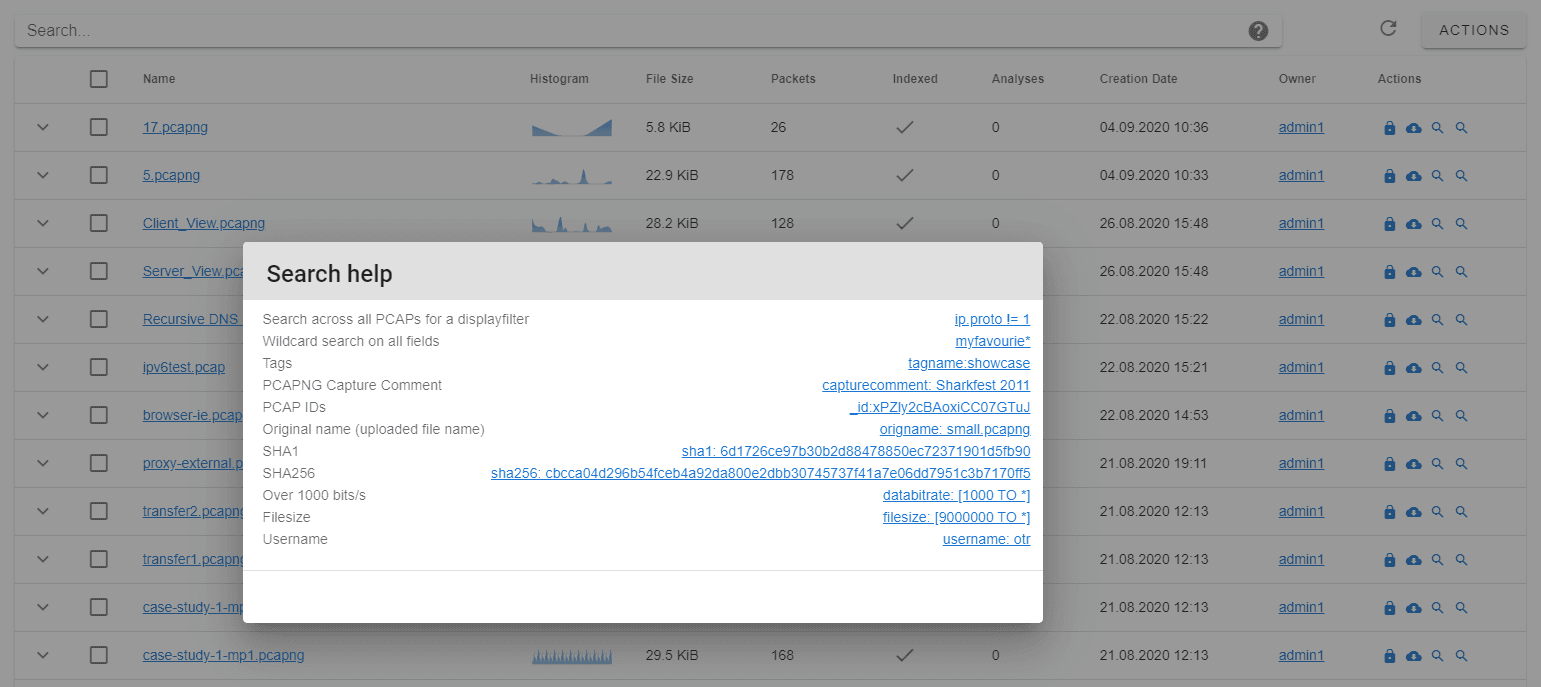
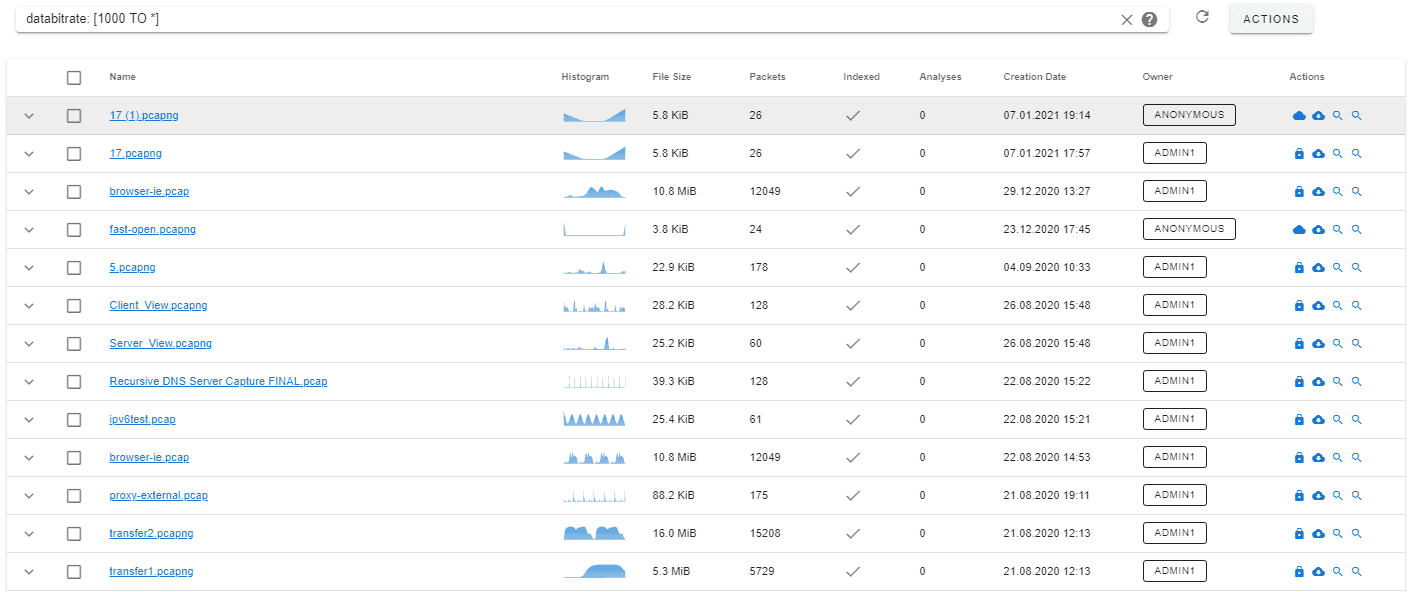
databitrate: [1000 TO *] - File size:
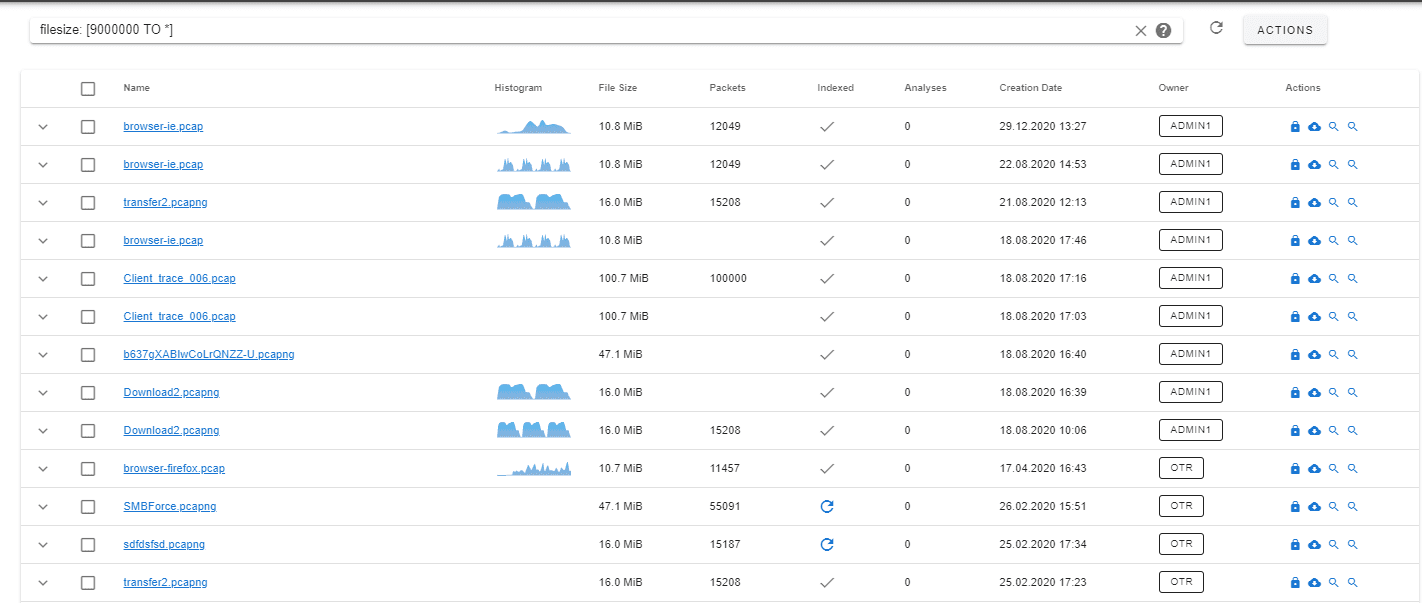
filesize: [90000 TO *]
Wildcard search
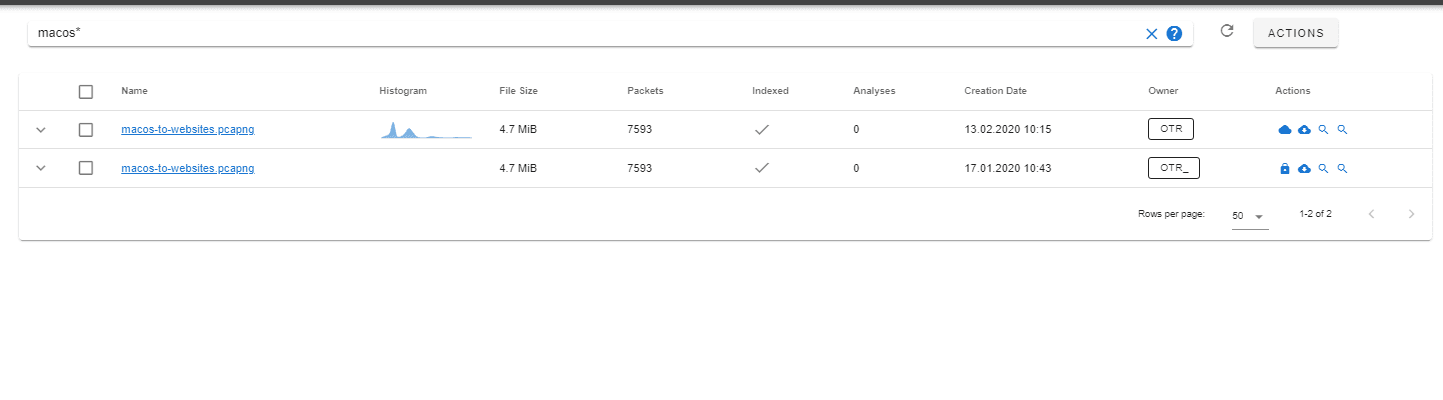
By using wildcard search you can search in multiple fields at once using a prefix.
Tag search
By using tagname you can search for PCAPs with a specific tag associated with them.
tagname: sharkfest2019
Indexed search ⚡️
Do an instant deep packet search through all your PCAPs at once
Indexed search leverages the index created for the PCAPs to search through the packets. Indexed search only supports field names that are indexed. You can use normal display filters to search through the PCAPs.
- Certain IP adresses:
ip.src == 1.1.1.1 or ip.dst == 1.1.1.1 - All PCAPs with retransmissions:
tcp.analysis.retransmission > 0 - All PCAPs having ICMP packets:
ip.proto == 1
The resulting PCAP list will include a column that shows how many of the packets in the PCAPs matched your query. To see which field names are indexed open the indicies view of the PCAP or the indexer profile settings page
Caveats
Different PCAPs might be indexed with different indexer configurations. If a field was not index by the default indexing process, reindexing might be necessary.
Some display filters may have surprising results or may not work. In general protocol or field-existence is not indexed. This means that the following filters that work in the packet list, do not work in the PCAP list:
tcphttptcp.analysis.flags
In the PCAP list, you always need to compare to a value. The above filters may be rewritten as follows to get a similar result:
ip.proto == 6 or ipv6.next_header == 6tcp.srcport == 80 or tcp.dstport == 80 or tcp.srcport == 443 or tcp.dstport == 443tcp.analysis.flags == 1
Filters that contains special characters like : or \ may not work, you can try to substitute the character with a wildcard:
eth.src== "00\:10\:a4\:de\:b5\:d0"eth.src == "00\:07\:50*"ipv6.src == "fe80\:\:b2ea\:bcff\:fe45\:b870"

